We love conversations with our clients – but it's our work that does the real talking.
“We needed help it was only a phone call away”
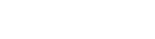
“We enjoyed another successful year at Hoag Library in no small part due to our relationship with Info Advantage. With the help of Johnathan and Linda we replaced many of our computers this year and have finally gotten all of our equipment onto a three year cycle for replacement. The installation of the new computers was handled in house knowing that if we needed help it was only a phone call away. Jeremiah was instrumental in helping us get all of the new equipment online and swapping out some other equipment with items that were at the end of life. Other times we have depended on Jacob to help us figure out why we were having problems. (an unknown power outage was one cause.) and he and Kris reset programs when we could not make successful updates. We were also unable to catalog new books when the dedicated computer went down. We sent the computer to IA , they performed “magic” and Jacob returned it and reinstalled it until our new computers came in.”

BETTY SUE MILLER
Director Hoag Library
“Words can’t describe the difference Info Advantage has made."
“I have been working with the Info Advantage team for a little over a year now as the IT Manager for VP Supply Corp. Words cannot describe the difference Info Advantage has made in my ability to do my job and protect our network and information assets. What started as a hardware vendor has now evolved into providing MSSP services to better protect our network – and we could not be happier with the quick return on investment this has given us. I would like to give a special shout-out to the members of the Info Advantage team who have not only done their job exceptionally well but have also mastered the soft skills and make me feel as though I can always reach out if we need them. Johnathan, Chris Chan, Chris McDonald, and Nick Wetherwax have been outstanding over the past year. With continued success like this VP Supply will have Info Advantage as a partner for many, many years to come!”

ADAM DEKRAMER
IT Manager VP Supply Corp
“I’ve worked with Info Advantage for 12 yrs. across multiple companies.”
“I have worked with Info Advantage over the past 12 years at a couple of companies. This year, Info Advantage helped me deploy a new VMWare / EMC environment for my current employer. During the selection process, they were very responsive with quote changes, responses to questions and updates explaining every aspect of the roll-out. They were very willing to take my current level of knowledge into consideration in the quoting process and their quotes were very competitive. Once awarded the project, Info Advantage proceeded very quickly to order and install the hardware in agreed time with on-hands training and system documentation for me. I would personally recommend Info Advantage for any project.”

CLINT SCHWAB
Durst Imaging / Rochester, NY

Always-On IT & Cybersecurity Protection
We deliver managed IT and cybersecurity solutions that protect your business, ensure regulatory compliance, and minimize risk so you can operate with confidence and focus on what drives your success.
iaGuardian Suite

UC: Seamless Connectivity
Scalable, seamless communication that boosts collaboration and keeps teams connected.

MSP: Transform IT Challenges
24/7 support, strong security, and cost-effective IT transforming your technology challenges into growth.

DR: Business Continuity
Stay resilient. Prevent data loss and downtime with expert support and advanced recovery.

Cloud: Secure Agile. Efficient.
Secure, scalable access to apps and data—anytime, anywhere—with built-in efficiency and cost savings.

Secure: Elite Cyber Protection
Always-on threat detection and real-time human response to stop attacks before they spread.












Industries We Empower
With decades of hands-on experience across regulated and fast-moving industries, we understand the unique risks you face. Our deep industry expertise allows us to deliver cybersecurity-first, compliance-ready IT solutions tailored to your environment and built to protect what matters most.

Financial Service Organizations

Healthcare &
Medical

Manufacturing &
Distribution

Legal Firms &
Attorneys

Nonprofit
Organizations

Professional
Services
Industries We Empower
With decades of hands-on experience across regulated and fast-moving industries, we understand the unique risks you face. Our deep industry expertise allows us to deliver cybersecurity-first, compliance-ready IT solutions tailored to your environment and built to protect what matters most.
More Insights
Stay connected with all of the latest IT trends and alerts by subscribing to our blog.

Complex Systems. Critical Data. And Cyber Threats on Tap.
Brews & Cyber Threats: Cybersecurity Awareness for Engineers
From civil to mechanical to electrical, engineers are the architects of infrastructure, innovation, and industry. But as the engineering field embraces cloud platforms, digital modeling, IoT-connected systems, and collaborative tools, one thing becomes clear: your data is now a target.
Whether you’re submitting municipal bids, managing sensitive schematics, or working on multi-million dollar R&D projects, your files and systems are highly valuable—and vulnerable.
That’s why Info Advantage created Brews & Cyber Threats, a cybersecurity awareness campaign with a twist. We’re pairing the top five digital threats facing engineering firms with handcrafted brews from Rohrbach Brewing Company in Rochester to make cybersecurity education stick.
Because precision matters, in your work and your security.
1. Scotch Ale + Phishing (Deceptively Smooth)
Phishing emails are increasingly polished. In a deadline-driven engineering environment, they often succeed.
Why It Hurts Engineers:
Login credentials for critical platforms get stolen
Malware is installed on shared CAD or modeling systems
Attackers gain access to client or infrastructure data
Info Advantage Tip:
Train all staff to detect social engineering and phishing tactics
Deploy MFA and email protection tools
Run monthly phishing simulations to reinforce habits
Why Scotch Ale?
Rohrbach’s Scotch Ale is malty and mellow, inviting at first but stronger than it looks—just like phishing, which hides its sting behind a smooth façade.
2. Space Kitty + Ransomware (Bold and Unforgiving)
Ransomware doesn’t just lock files; it halts operations. If project files, simulation results, or client correspondence get encrypted, everything stops.
Why It Hurts Engineers:
Downtime on projects worth millions
Loss of intellectual property and operational plans
Missed deadlines, client dissatisfaction, and financial loss
Info Advantage Tip:
Backup all data regularly and test recovery processes
Install EDR solutions that detect and isolate ransomware
Keep CAD suites and document storage patched
Why Space Kitty?
This bold double IPA hits like ransomware—intensely and without warning. You’ll feel it if you’re not prepared.
3. Blueberry Ale + Business Email Compromise (BEC) (Sweet, Crisp, and a Little Sneaky)
BEC scams look ordinary: a fake email from a lead engineer, a fraudulent payment change from a subcontractor. One slip can be costly.
Why It Hurts Engineers:
Fraudulent wire transfers to “vendors” or consultants
Leaked project estimates or sensitive infrastructure data
Subcontractor and partner trust compromised
Info Advantage Tip:
Use dual-approval for financial transactions and password changes
Implement SPF, DKIM, and DMARC for email authentication
Educate project managers and finance leads on spotting deception
Why Blueberry Ale?
Light, crisp, and easy to underestimate—much like BEC attacks. The sweetness hides a deeper bite.
4. Helles Lager + Insider Threats (Smooth, But Needs Guardrails)
Not all risks come from the outside. Employees, ex-staff, or contractors mishandling specs can cause serious damage.
Why It Hurts Engineers:
Theft of proprietary designs
Non-compliance with client data policies
Risk to intellectual property and patents
Info Advantage Tip:
Apply role-based access to project folders and file systems
Remove access immediately when employees leave
Monitor file activity and flag high-risk behavior
Why Helles Lager?
Rohrbach’s Helles Lager is clean and smooth—but like trusted team members, it still needs structure and guardrails.
5. Vanilla Porter + Cloud Misconfigurations (Complex, Layered, and Needs Precision)
Engineering firms now store designs, 3D models, simulations, and deliverables in the cloud. Misconfigurations in Google Drive, Microsoft 365, Box, or BIM platforms can leave data exposed.
Why It Hurts Engineers:
Proprietary plans or contracts accidentally made public
Compliance violations with partners or clients
Unauthorized access to live documents or workflows
Info Advantage Tip:
Conduct regular audits of cloud storage and permissions
Use encryption, MFA, and activity logging
Set default permissions to “least privilege” by role
Why Vanilla Porter?
Complex and layered, like your cloud setup. When handled right, it’s smooth and rewarding. When neglected, it turns sour fast.
Final Sip: Secure Your Specs, Clients, and Firm
Your engineering work powers cities, bridges, and innovation. But even the strongest designs can be compromised by a weak password or misconfiguration.
Let’s build a better foundation—starting with your firm’s cybersecurity.
Engineers thrive on precision. So does cybersecurity.
Uncover strategies to protect your data and IP while enjoying expertly paired craft beers.
Don't miss our upcoming event to hear this all live and in person!
RSVP here: Spots are limited—reserve your seat here!